References:
http://www.server-world.info/en/note?os=CentOS_6&p=ldap&f=1
http://www.server-world.info/en/note?os=CentOS_6&p=ldap&f=2
http://www.server-world.info/en/note?os=CentOS_6&p=samba&f=4
Very good tutorials on references link above, im just practice them..
Skenario:
IP Address Server: 192.168.10.6
I. Install OpenLDAP
# yum -y install openldap-servers openldap-clients
# vi /etc/sysconfig/ldap
Line 12: uncomment and change
# Run slapd with -h "... ldapi:/// ..."
# yes/no, default: yes
SLAPD_LDAPI=yes
# vi /etc/openldap/slapd.conf
Create new
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
# rm -rf /etc/openldap/slapd.d/*
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d
config file testing succeeded
# vi /etc/openldap/slapd.d/cn=config/olcDatabase\={0}config.ldif
Line 4: change:
olcAccess: {0} to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth manage by * break
# vi /etc/openldap/slapd.d/cn=config/olcDatabase\={1}monitor.ldif
Create new:
dn: olcDatabase={1}monitor
objectClass: olcDatabaseConfig
olcDatabase: {1}monitor
olcAccess: {1}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth manage by * break
olcAddContentAcl: FALSE
olcLastMod: TRUE
olcMaxDerefDepth: 15
olcReadOnly: FALSE
olcMonitoring: FALSE
structuralObjectClass: olcDatabaseConfig
creatorsName: cn=config
modifiersName: cn=config
# chown -R ldap. /etc/openldap/slapd.d
# chmod -R 700 /etc/openldap/slapd.d
# service slapd start
# chkconfig slapd on
II. Initial Configuration
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/core.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=core,cn=schema,cn=config"
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=cosine,cn=schema,cn=config"
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=nis,cn=schema,cn=config"
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=inetorgperson,cn=schema,cn=config"
# slappasswd
New password:
Re-enter new password:
{SSHA}TcZS9sd8xsESRtBzMrhfsOHqPELWh0l5
# mkdir /tmp/setldap ; cd /tmp/setldap
# vi backend.ldif
Create new:
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulepath: /usr/lib64/openldap
olcModuleload: back_hdb
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {2}hdb
olcSuffix: dc=tahubachem,dc=local
olcDbDirectory: /var/lib/ldap
olcRootDN: cn=Manager,dc=tahubachem,dc=local
olcRootPW: {SSHA}TcZS9sd8xsESRtBzMrhfsOHqPELWh0l5
olcDbConfig: set_cachesize 0 2097152 0
olcDbConfig: set_lk_max_objects 1500
olcDbConfig: set_lk_max_locks 1500
olcDbConfig: set_lk_max_lockers 1500
olcDbIndex: objectClass eq
olcLastMod: TRUE
olcMonitoring: TRUE
olcDbCheckpoint: 512 30
olcAccess: to attrs=userPassword by dn="cn=Manager,dc=tahubachem,dc=local" write by anonymous auth by self write by * none
olcAccess: to attrs=shadowLastChange by self write by * read
olcAccess: to dn.base="" by * read
olcAccess: to * by dn="cn=Manager,dc=tahubachem,dc=local" write by * read
# ldapadd -Y EXTERNAL -H ldapi:/// -f backend.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=module,cn=config"
adding new entry "olcDatabase=hdb,cn=config"
# vi frontend.ldif
Create new:
dn: dc=tahubachem,dc=local
objectClass: top
objectClass: dcObject
objectclass: organization
o: tahubachem
dc: tahubachem
dn: cn=Manager,dc=tahubachem,dc=local
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: Manager
userPassword: {SSHA}TcZS9sd8xsESRtBzMrhfsOHqPELWh0l5
dn: ou=people,dc=tahubachem,dc=local
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=tahubachem,dc=local
objectClass: organizationalUnit
ou: groups
# ldapadd -x -D cn=Manager,dc=tahubachem,dc=local -W -f frontend.ldif
Enter LDAP Password:
adding new entry "dc=tahubachem,dc=local"
adding new entry "cn=Manager,dc=tahubachem,dc=local"
adding new entry "ou=people,dc=tahubachem,dc=local"
adding new entry "ou=groups,dc=tahubachem,dc=local"
III. Add Existing local Users to LDAP Directory
# vi ldapuser.sh
# extract local users who have 500-999 digit UID
# replace "SUFFIX=***" to your own suffix
# this is an example
#!/bin/bash
SUFFIX='dc=tahubachem,dc=local'
LDIF='ldapuser.ldif'
echo -n > $LDIF
for line in `grep "x:[5-9][0-9][0-9]:" /etc/passwd | sed -e "s/ /%/g"`
do
UID1=`echo $line | cut -d: -f1`
NAME=`echo $line | cut -d: -f5 | cut -d, -f1`
if [ ! "$NAME" ]
then
NAME=$UID1
else
NAME=`echo $NAME | sed -e "s/%/ /g"`
fi
SN=`echo $NAME | awk '{print $2}'`
if [ ! "$SN" ]
then
SN=$NAME
fi
GIVEN=`echo $NAME | awk '{print $1}'`
UID2=`echo $line | cut -d: -f3`
GID=`echo $line | cut -d: -f4`
PASS=`grep $UID1: /etc/shadow | cut -d: -f2`
SHELL=`echo $line | cut -d: -f7`
HOME=`echo $line | cut -d: -f6`
EXPIRE=`passwd -S $UID1 | awk '{print $7}'`
FLAG=`grep $UID1: /etc/shadow | cut -d: -f9`
if [ ! "$FLAG" ]
then
FLAG="0"
fi
WARN=`passwd -S $UID1 | awk '{print $6}'`
MIN=`passwd -S $UID1 | awk '{print $4}'`
MAX=`passwd -S $UID1 | awk '{print $5}'`
LAST=`grep $UID1: /etc/shadow | cut -d: -f3`
echo "dn: uid=$UID1,ou=people,$SUFFIX" >> $LDIF
echo "objectClass: inetOrgPerson" >> $LDIF
echo "objectClass: posixAccount" >> $LDIF
echo "objectClass: shadowAccount" >> $LDIF
echo "uid: $UID1" >> $LDIF
echo "sn: $SN" >> $LDIF
echo "givenName: $GIVEN" >> $LDIF
echo "cn: $NAME" >> $LDIF
echo "displayName: $NAME" >> $LDIF
echo "uidNumber: $UID2" >> $LDIF
echo "gidNumber: $GID" >> $LDIF
echo "userPassword: {crypt}$PASS" >> $LDIF
echo "gecos: $NAME" >> $LDIF
echo "loginShell: $SHELL" >> $LDIF
echo "homeDirectory: $HOME" >> $LDIF
echo "shadowExpire: $EXPIRE" >> $LDIF
echo "shadowFlag: $FLAG" >> $LDIF
echo "shadowWarning: $WARN" >> $LDIF
echo "shadowMin: $MIN" >> $LDIF
echo "shadowMax: $MAX" >> $LDIF
echo "shadowLastChange: $LAST" >> $LDIF
echo >> $LDIF
done
# sh ldapuser.sh
# ldapadd -x -D cn=Manager,dc=tahubachem,dc=local -W -f ldapuser.ldif
Enter LDAP Password:
IV. Add existing local groups to LDAP directory.
# vi ldapgroup.sh
# extract local groups who have 500-999 digit UID
# replace "SUFFIX=***" to your own suffix
# this is an example
#!/bin/bash
SUFFIX='dc=tahubachem,dc=local'
LDIF='ldapgroup.ldif'
echo -n > $LDIF
for line in `grep "x:[5-9][0-9][0-9]:" /etc/group`
do
CN=`echo $line | cut -d: -f1`
GID=`echo $line | cut -d: -f3`
echo "dn: cn=$CN,ou=groups,$SUFFIX" >> $LDIF
echo "objectClass: posixGroup" >> $LDIF
echo "cn: $CN" >> $LDIF
echo "gidNumber: $GID" >> $LDIF
users=`echo $line | cut -d: -f4 | sed "s/,/ /g"`
for user in ${users} ; do
echo "memberUid: ${user}" >> $LDIF
done
echo >> $LDIF
done
# sh ldapgroup.sh
# ldapadd -x -D cn=Manager,dc=tahubachem,dc=local -W -f ldapgroup.ldif
Enter LDAP Password:
V. Configuration for LDAP client
# yum -y install openldap-clients nss-pam-ldapd
# vi /etc/openldap/ldap.conf
BASE dc=tahubachem,dc=local
URI ldap://192.168.10.6/
TLS_CACERTDIR /etc/openldap/cacerts
# vi /etc/nslcd.conf
Line 131: specify URI, Suffix
uri ldap://192.168.10.6/
base dc=tahubachem,dc=local
ssl no
tls_cacertdir /etc/openldap/cacerts
# vi /etc/pam_ldap.conf
Line 17: make it comment
host 127.0.0.1
Line 20: specify Suffix
base dc=tahubachem,dc=local
Add at the last line
uri ldap://192.168.10.6/
ssl no
tls_cacertdir /etc/openldap/cacerts
pam_password md5
# vi /etc/pam.d/system-auth
add highlight parameter line 8,14,19,26,28
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth sufficient pam_fprintd.so
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 500 quiet
auth sufficient pam_ldap.so use_first_pass
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 500 quiet
account [default=bad success=ok user_unknown=ignore] pam_ldap.so
account required pam_permit.so
password requisite pam_cracklib.so try_first_pass retry=3 type=
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok
password sufficient pam_ldap.so use_authtok
password required pam_deny.so
session optional pam_keyinit.so revoke
session required pam_limits.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
session required pam_unix.so
session optional pam_ldap.so
# add if you need ( create home directory automatically if it's none )
session optional pam_mkhomedir.so skel=/etc/skel umask=077
# vi /etc/nsswitch.conf
Line 33: add:
passwd: files ldap
shadow: files ldap
group: files ldap
Line 57: change:
netgroup: ldap
Line 61: change:
automount: files ldap
# vi /etc/sysconfig/authconfig
Line 18: change:
USELDAP=yes
# chkconfig nslcd on
# shutdown -r now
VI. Change OpenLDAP settings
# mkdir /tmp/setsamba
# cd /tmp/setsamba
-Install samba from centos default repo, check the samba version then do wget
# yum -y install samba
# wget http://mirror.centos.org/centos/6.3/os/x86_64/Packages/samba-3.5.10-125.el6.x86_64.rpm
# rpm2cpio samba-3.5.10-125.el6.x86_64.rpm | cpio -id
# cp ./etc/openldap/schema/samba.schema /etc/openldap/schema/
# vi schema_convert.conf
Create new:
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/collective.schema
include /etc/openldap/schema/corba.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/duaconf.schema
include /etc/openldap/schema/dyngroup.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/java.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
include /etc/openldap/schema/ppolicy.schema
include /etc/openldap/schema/samba.schema
# mkdir /tmp/setsamba/ldif_output
# slapcat -f schema_convert.conf -F /tmp/setsamba/ldif_output -n0 -s "cn={12}samba,cn=schema,cn=config" > ./cn=samba.ldif
# vi cn=samba.ldif
Line 1,3: change ( remove “{12}” )
dn: cn=samba,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: samba
Remove these lines below ( placed at the bottom )
structuralObjectClass: olcSchemaConfig
entryUUID: 761ed782-e76d-102f-94de-7784c8a781ec
creatorsName: cn=config
createTimestamp: 20110320184149Z
entryCSN: 20110320184149.954974Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20110320184149Z
# ldapadd -Y EXTERNAL -H ldapi:/// -f cn=samba.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=samba,cn=schema,cn=config"
# vi samba_indexes.ldif
Create new
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcDbIndex
olcDbIndex: uidNumber eq
olcDbIndex: gidNumber eq
olcDbIndex: loginShell eq
olcDbIndex: uid eq,pres,sub
olcDbIndex: memberUid eq,pres,sub
olcDbIndex: uniqueMember eq,pres
olcDbIndex: sambaSID eq
olcDbIndex: sambaPrimaryGroupSID eq
olcDbIndex: sambaGroupType eq
olcDbIndex: sambaSIDList eq
olcDbIndex: sambaDomainName eq
olcDbIndex: default sub
# ldapmodify -Y EXTERNAL -H ldapi:/// -f samba_indexes.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}hdb,cn=config"
# service slapd restart
VII. Change Samba settings. This Samba PDC server need to be a LDAP Client.
# yum --enablerepo=epel -y install smbldap-tools
# mv /etc/samba/smb.conf /etc/samba/smb.conf.bak
# cp /usr/share/doc/smbldap-tools-*/smb.conf /etc/samba/smb.conf
# vi /etc/samba/smb.conf
# Global parameters
[global]
workgroup = TAHUBACHEM
netbios name = KUCING
security = user
enable privileges = yes
#interfaces = 192.168.5.11
#username map = /etc/samba/smbusers
server string = Samba Server %v
#security = ads
encrypt passwords = Yes
min passwd length = 3
#pam password change = no
#obey pam restrictions = No
# method 1:
#unix password sync = no
#ldap passwd sync = yes
# method 2:
unix password sync = yes
ldap passwd sync = yes
passwd program = /usr/sbin/smbldap-passwd -u “%u”
passwd chat = “Changing *\nNew password*” %n\n “*Retype new password*” %n\n”
log level = 0
syslog = 0
log file = /var/log/samba/log.%U
max log size = 100000
time server = Yes
socket options = TCP_NODELAY SO_RCVBUF=8192 SO_SNDBUF=8192
mangling method = hash2
Dos charset = CP932
Unix charset = UTF-8
logon script = logon.bat
logon drive = W:
logon home =
logon path =
domain logons = Yes
domain master = Yes
os level = 65
preferred master = Yes
wins support = yes
# passdb backend = ldapsam:”ldap://ldap1.company.com ldap://ldap2.company.com”
passdb backend = ldapsam:ldap://192.168.10.6/
ldap admin dn = cn=Manager,dc=tahubachem,dc=local
#ldap admin dn = cn=samba,ou=DSA,dc=company,dc=com
ldap suffix = dc=tahubachem,dc=local
ldap group suffix = ou=groups
ldap user suffix = ou=people
ldap machine suffix = ou=Computers
ldap idmap suffix = ou=Idmap
add user script = /usr/sbin/smbldap-useradd -m “%u”
#ldap delete dn = Yes
delete user script = /usr/sbin/smbldap-userdel “%u”
add machine script = /usr/sbin/smbldap-useradd -t 0 -w “%u”
add group script = /usr/sbin/smbldap-groupadd -p “%g”
delete group script = /usr/sbin/smbldap-groupdel “%g”
add user to group script = /usr/sbin/smbldap-groupmod -m “%u” “%g”
delete user from group script = /usr/sbin/smbldap-groupmod -x “%u” “%g”
set primary group script = /usr/sbin/smbldap-usermod -g ‘%g’ ‘%u’
admin users = sysadmin
ldap ssl = no
# printers configuration
#printer admin = @”Print Operators”
load printers = Yes
create mask = 0640
directory mask = 0750
#force create mode = 0640
#force directory mode = 0750
nt acl support = No
printing = cups
printcap name = cups
deadtime = 10
guest account = nobody
map to guest = Bad User
dont descend = /proc,/dev,/etc,/lib,/lost+found,/initrd
show add printer wizard = yes
; to maintain capital letters in shortcuts in any of the profile folders:
preserve case = yes
short preserve case = yes
case sensitive = no
[netlogon]
path = /home/netlogon/
browseable = No
read only = yes
[profiles]
path = /home/profiles
read only = no
create mask = 0600
directory mask = 0700
browseable = No
guest ok = Yes
profile acls = yes
csc policy = disable
# next line is a great way to secure the profiles
#force user = %U
# next line allows administrator to access all profiles
#valid users = %U “Domain Admins”
[printers]
comment = Network Printers
#printer admin = @”Print Operators”
guest ok = yes
printable = yes
path = /home/spool/
browseable = No
read only = Yes
printable = Yes
print command = /usr/bin/lpr -P%p -r %s
lpq command = /usr/bin/lpq -P%p
lprm command = /usr/bin/lprm -P%p %j
# print command = /usr/bin/lpr -U%U@%M -P%p -r %s
# lpq command = /usr/bin/lpq -U%U@%M -P%p
# lprm command = /usr/bin/lprm -U%U@%M -P%p %j
# lppause command = /usr/sbin/lpc -U%U@%M hold %p %j
# lpresume command = /usr/sbin/lpc -U%U@%M release %p %j
# queuepause command = /usr/sbin/lpc -U%U@%M stop %p
# queueresume command = /usr/sbin/lpc -U%U@%M start %p
[print$]
path = /home/printers
guest ok = No
browseable = Yes
read only = Yes
valid users = @”Print Operators”
write list = @”Print Operators”
create mask = 0664
directory mask = 0775
[public]
path = /datasamba/public
guest ok = yes
browseable = Yes
writable = yes
force create mode = 0775
force directory mode = 0775
[private]
path = /datasamba/private
guest ok = yes
browseable = Yes
writable = yes
force create mode = 0770
force directory mode = 0770
# mkdir /datasamba
# mkdir /datasamba/public
# mkdir /datasamba/private
# mkdir /home/netlogon
# service smb restart
# service nmb restart
# chkconfig smb on
# chkconfig nmb on
# smbpasswd -W
Setting stored password for "cn=Manager,dc=tahubachem,dc=local" in secrets.tdb
New SMB password:
Retype new SMB password:
# perl /usr/share/doc/smbldap-tools-*/configure.pl
[root@ayam setsamba]# perl /usr/share/doc/smbldap-tools-*/configure.pl
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
smbldap-tools script configuration
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Before starting, check
. if your samba controller is up and running.
. if the domain SID is defined (you can get it with the ‘net getlocalsid’)
. you can leave the configuration using the Ctrl-c key combination
. empty value can be set with the “.” character
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Looking for configuration files…
Samba Configuration File Path [/etc/samba/smb.conf] > # Enter
The default directory in which the smbldap configuration files are stored is shown.
If you need to change this, enter the full directory path, then press enter to continue.
Smbldap-tools Configuration Directory Path [/etc/smbldap-tools] >
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Let’s start configuring the smbldap-tools scripts …
. workgroup name: name of the domain Samba acts as a PDC for
workgroup name [TAHUBACHEM] > # Enter
. netbios name: netbios name of the samba controller
netbios name [KUCING] > # Enter
. logon drive: local path to which the home directory will be connected (for NT Workstations). Ex: ‘H:’
logon drive [W:] > # Enter
. logon home: home directory location (for Win95/98 or NT Workstation).
(use %U as username) Ex:’\\KUCING\%U’
logon home (press the “.” character if you don’t want homeDirectory) [\\KUCING\%U] > . # input a period
. logon path: directory where roaming profiles are stored. Ex:’\\KUCING\profiles\%U’
logon path (press the “.” character if you don’t want roaming profiles) [\\KUCING\profiles\%U] > . # input a period
. home directory prefix (use %U as username) [/home/%U] > # Enter
. default users’ homeDirectory mode [700] > # Enter
. default user netlogon script (use %U as username) [logon.bat] > # Enter
default password validation time (time in days) [45] > 90 # Enter
. ldap suffix [dc=tahubachem,dc=local] > # Enter
. ldap group suffix [ou=groups] > # Enter
. ldap user suffix [ou=people] > # Enter
. ldap machine suffix [ou=Computers] > # Enter
. Idmap suffix [ou=Idmap] > # Enter
. sambaUnixIdPooldn: object where you want to store the next uidNumber
and gidNumber available for new users and groups
sambaUnixIdPooldn object (relative to ${suffix}) [sambaDomainName=TAHUBACHEM] > # Enter
. ldap master server: IP address or DNS name of the master (writable) ldap server
ldap master server [192.168.10.6] > # Enter
. ldap master port [389] > # Enter
. ldap master bind dn [cn=Manager,dc=tahubachem,dc=local] > # Enter
. ldap master bind password [] > qwerty # input LDAP admin password then Enter
. ldap slave server: IP address or DNS name of the slave ldap server: can also be the master one
ldap slave server [192.168.10.6] > # specify LDAP slave’s IP (Enter with empy if none)
. ldap slave port [389] > # Enter
. ldap slave bind dn [cn=Manager,dc=tahubachem,dc=local] > # Enter
. ldap slave bind password [] > qwerty # Input if there is, if not input the same one with master
. ldap tls support (1/0) [0] > # Enter
. SID for domain TAHUBACHEM: SID of the domain (can be obtained with ‘net getlocalsid KUCING’)
SID for domain TAHUBACHEM [S-1-5-21-2056273974-4081619650-1090555569] > # Enter
. unix password encryption: encryption used for unix passwords
unix password encryption (CRYPT, MD5, SMD5, SSHA, SHA) [SSHA] > # Enter
. default user gidNumber [513] > # Enter
. default computer gidNumber [515] > # Enter
. default login shell [/bin/bash] > # Enter
. default skeleton directory [/etc/skel] > # Enter
. default domain name to append to mail address [] > # Enter
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
backup old configuration files:
/etc/smbldap-tools/smbldap.conf->/etc/smbldap-tools/smbldap.conf.old
/etc/smbldap-tools/smbldap_bind.conf->/etc/smbldap-tools/smbldap_bind.conf.old
writing new configuration file:
/etc/smbldap-tools/smbldap.conf done.
/etc/smbldap-tools/smbldap_bind.conf done.
[root@kucing setsamba]#
# smbldap-populate
[root@kucing setsamba]# smbldap-populate
Populating LDAP directory for domain TAHUBACHEM (S-1-5-21-2056273974-4081619650-1090555569)
(using builtin directory structure)
entry dc=tahubachem,dc=local already exist.
entry ou=people,dc=tahubachem,dc=local already exist.
entry ou=groups,dc=tahubachem,dc=local already exist.
adding new entry: ou=Computers,dc=tahubachem,dc=local
adding new entry: ou=Idmap,dc=tahubachem,dc=local
adding new entry: uid=root,ou=people,dc=tahubachem,dc=local
adding new entry: uid=nobody,ou=people,dc=tahubachem,dc=local
adding new entry: cn=Domain Admins,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Domain Users,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Domain Guests,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Domain Computers,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Administrators,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Account Operators,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Print Operators,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Backup Operators,ou=groups,dc=tahubachem,dc=local
adding new entry: cn=Replicators,ou=groups,dc=tahubachem,dc=local
entry sambaDomainName=TAHUBACHEM,dc=tahubachem,dc=local already exist. Updating it...
Please provide a password for the domain root:
Changing UNIX and samba passwords for root
New password:
Retype new password:
[root@kucing setsamba]#
-Setup firewall
# system-config-firewall-tui
Open port samba,samba client,customize => tcp:389
VIII. Testing
-Add samba ldap user
# smbldap-useradd -a -m sysadmin
# smbldap-groupmod -m sysadmin "Domain Admins"
# smbldap-passwd sysadmin
# smbldap-useradd -a -m bachem
# smbldap-groupmod -m bachem "Domain Admins"
# smbldap-passwd bachem
# smbldap-useradd -a -m staff1
# smbldap-groupmod -m staff1 "Domain Users"
# smbldap-passwd staff1
-Set ACL for samba share folder
# setfacl -m group:Domain\ Admins:rwx /datasamba/private/
# setfacl -m group:Domain\ Users:rwx /datasamba/public/
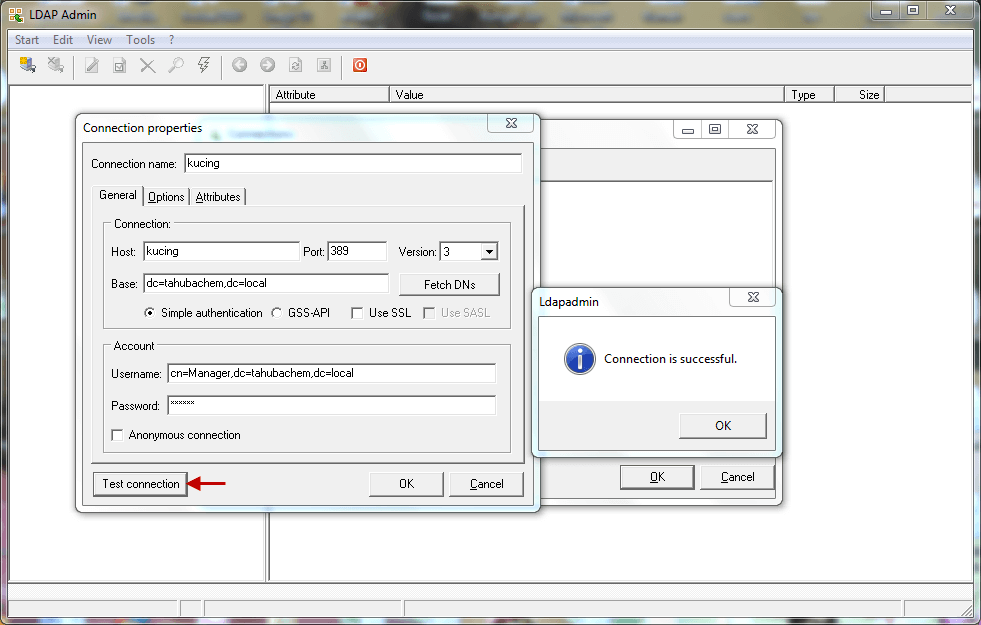
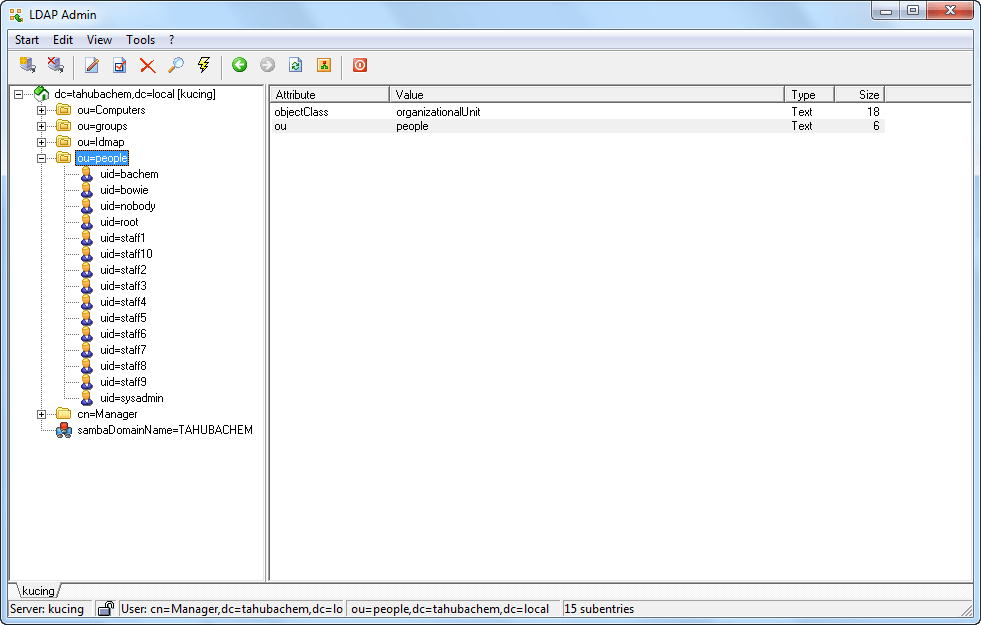
-Setup Windows LDAP Admin to make easier maintain ldap user
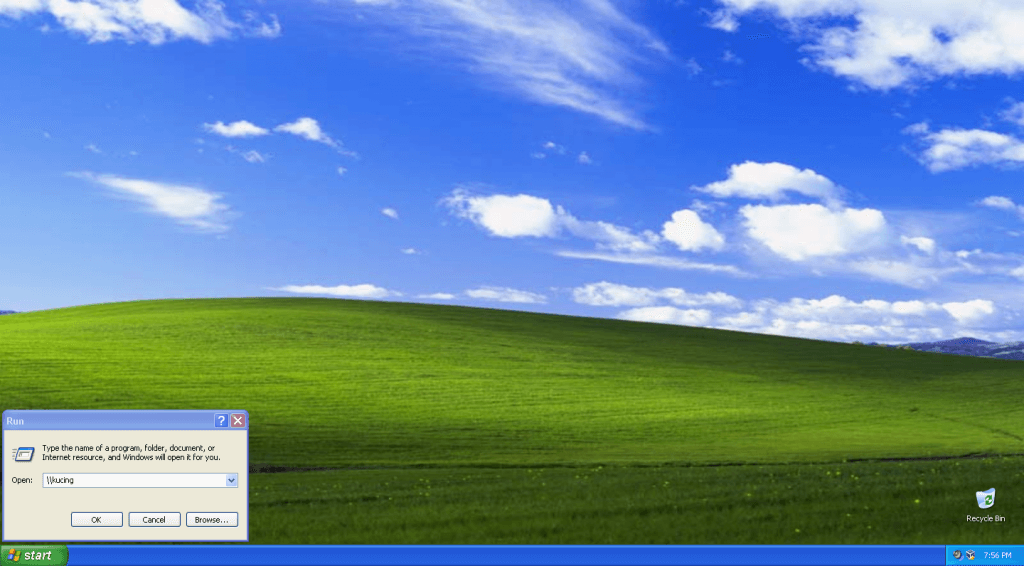
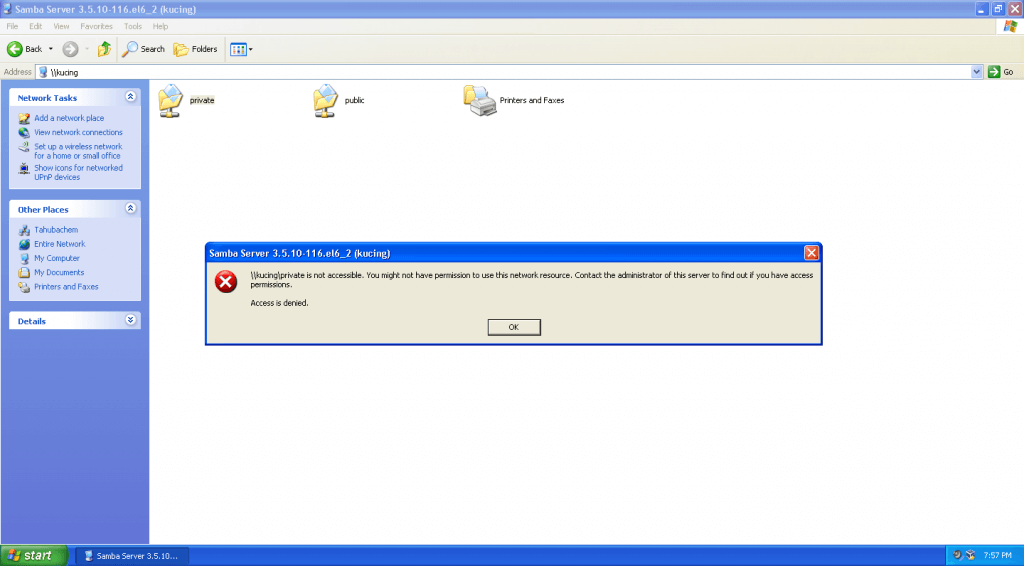
-Login as domain users to test share folder private
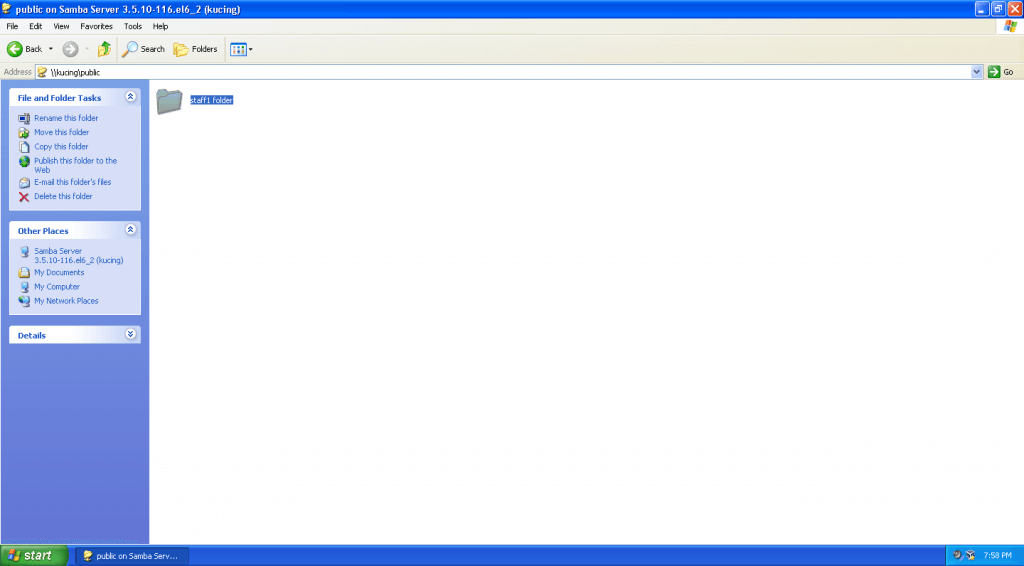
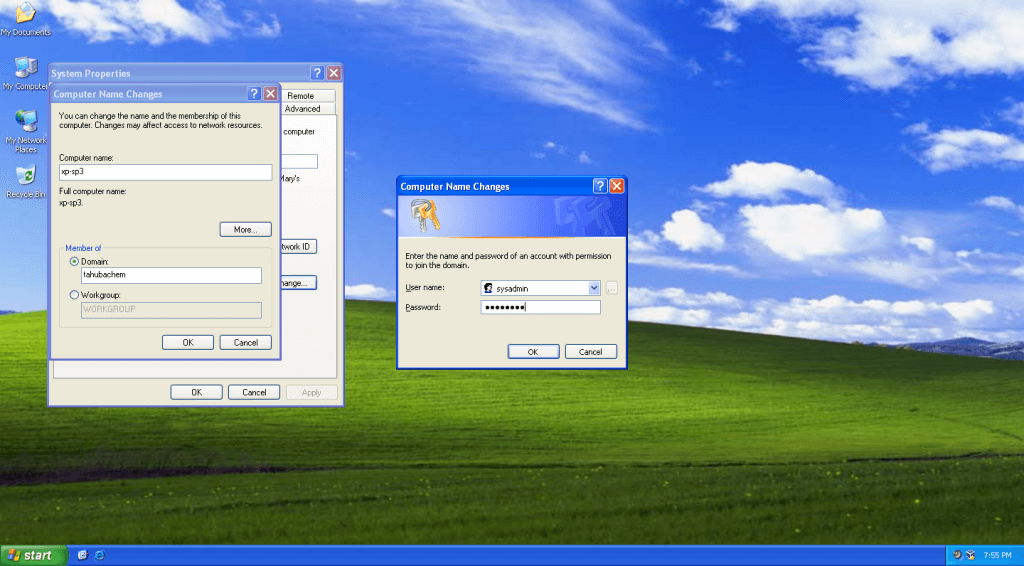
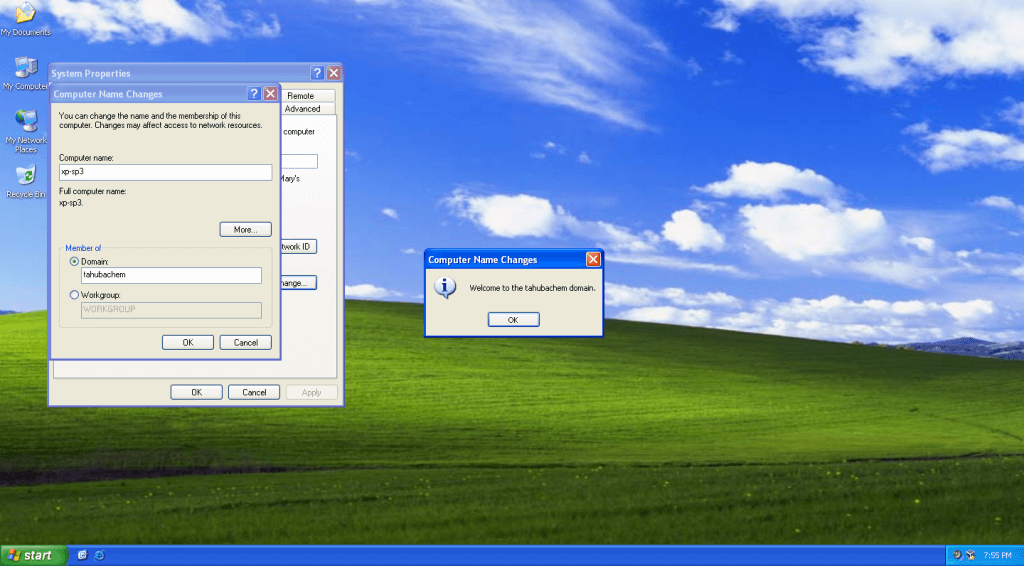
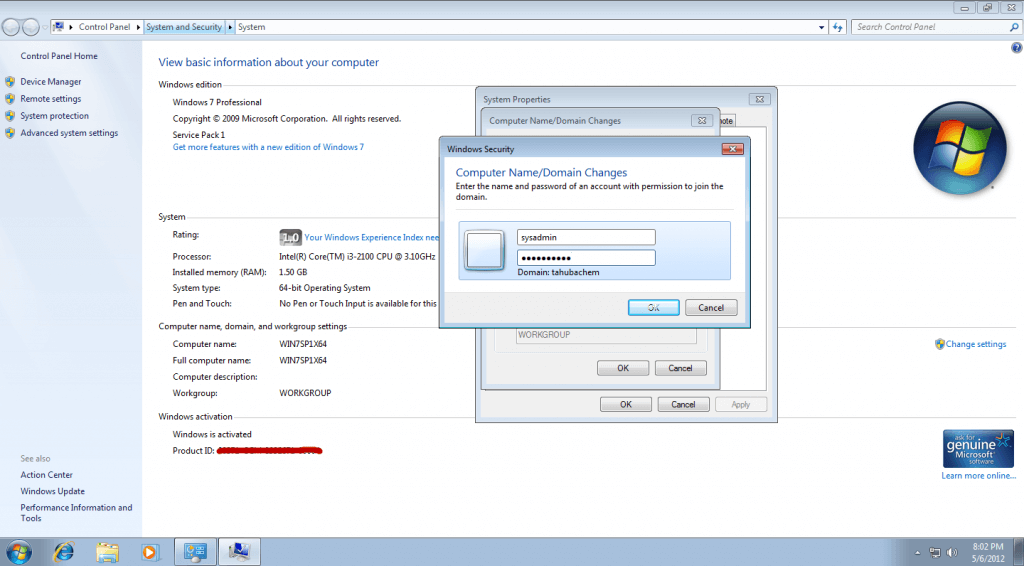
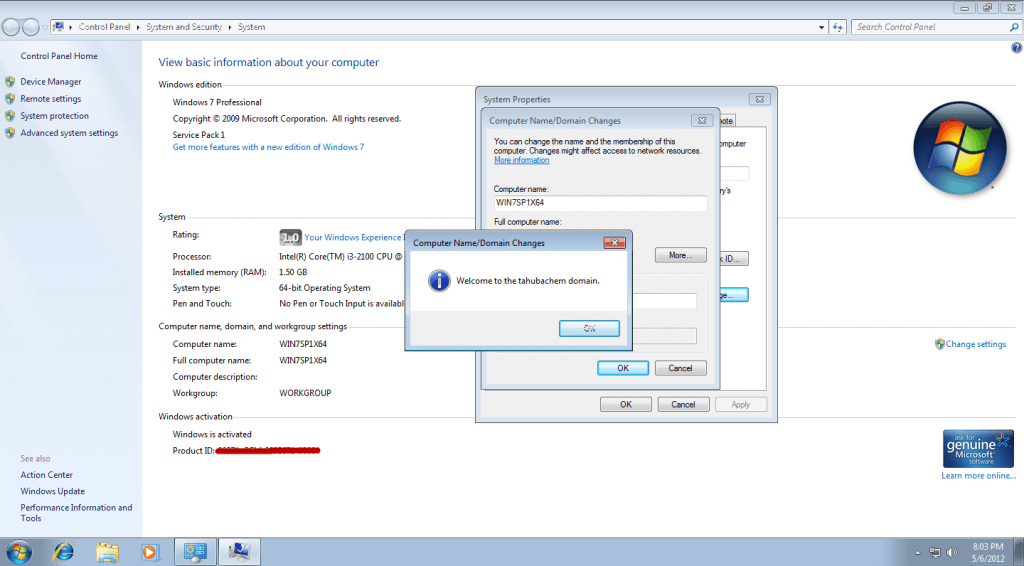
-Win 7 Pro x64 Join Domain:
Now join your Windows 7 PC to the domain using this official Samba mini guide http://wiki.samba.org/index.php/Windows7
-Download Windows7 Registry Patch from here:
https://bugzilla.samba.org/attachment.cgi?id=4988&action=view
-Note based in my experiences:
If computer with Windows7 fresh install with no update is going to join domain, first I’m install hotfix from here:
http://support.microsoft.com/hotfix/KBHotfix.aspx?kbnum=2171571&kbln=en-us then run registry patch Win7_Samba3DomainMember.reg => Restart PC => Join Domain =>> Restart PC => successful login with domain users
If Computer with Windows7 SP1, I just run registry patch Win7_Samba3DomainMember.reg => Restart PC => Join Domain => Restart PC => Successful login with domain users
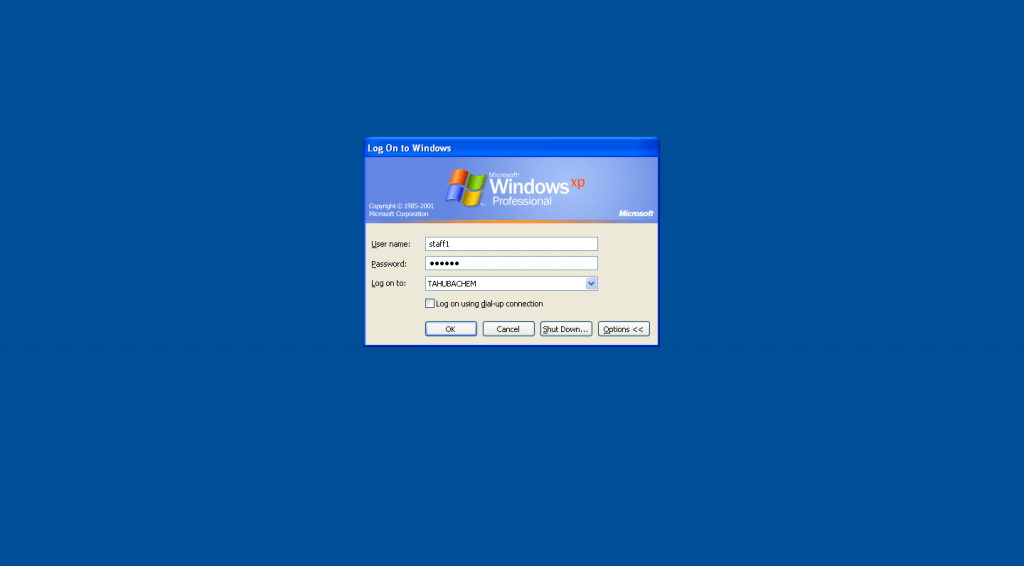
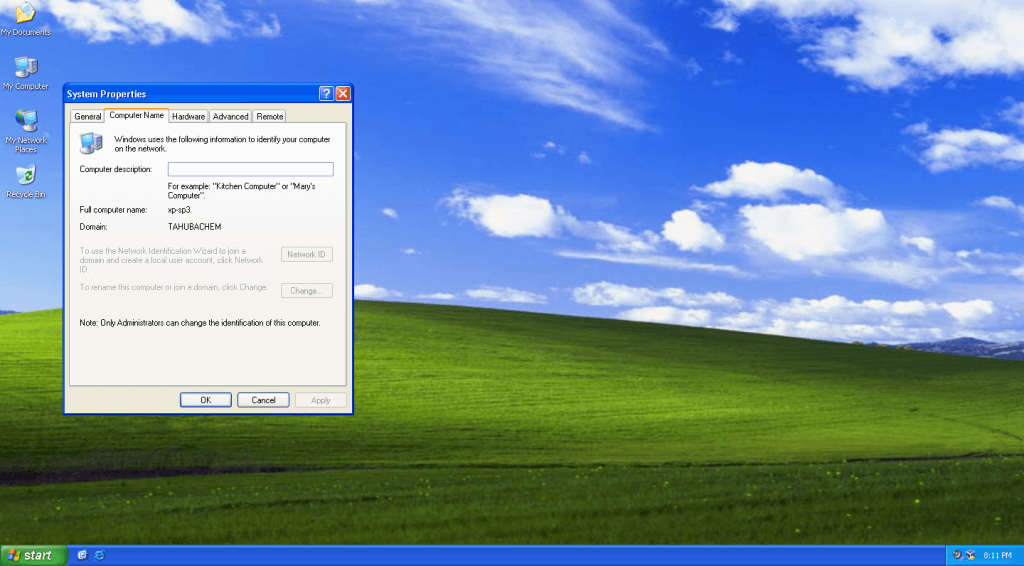
– Login as domain admins to test access share folder private



Hi,
I go through you instructions everything is working fine, But whe i try to add user account using
smbldap-useradd -a -m sysadmin . I am getting below error.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 15.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 19.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 25.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 35.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 40.
Use of uninitialized value $value in substitution (s///) at /usr/share/perl5/vendor_perl/smbldap_tools.pm line 144, line 85.
kindly help me . I am new to this setup
Thank you,
I resolved the issue. Solution is just remove the empty space on smb.conf file ( line 15 )
Dear Admin,
Pada step VI. Change OpenLDAP settings, ketika add samba.ldif saya mendapati error ldap_add: Naming violation (64) begini :
=======================================
=======================================
[root@xx setsamba]# ldapadd -Y EXTERNAL -H ldapi:/// -f cn=samba.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry “cn={}samba,cn=schema,cn=config”
ldap_add: Naming violation (64)
=======================================
Mohon bantuan dan solusinya.., Saya menggunakan Centos 6.2 32 bit
Terimakasih.
Salam
acenk90
Hai,
Salam do you have configuration for VPN in centos 6 and i want to connect my home system through from out of any where. Please send me the configuration doc to.
Thanks
T.Saminadane