Skenario:
Primary DNS : 192.168.99.5
Slave DNS : 192.168.99.6
II. Edit /etc/hosts
# vi /etc/hosts
127.0.0.1 localhost.localdomain localhost.localdomain localhost4 localhost4.localdomain4 localhost ns2
::1 localhost.localdomain localhost.localdomain localhost6 localhost6.localdomain6 localhost ns2
192.168.99.6 ns2.bachem.local ns2
III. Install & Setting Bind chroot for DNS Server
-Install Bind chroot
# yum -y install bind bind-chroot
-Setting iptables (open port DNS)
# system-config-firewall-tui
or
# iptables -A INPUT -p udp -m state --state NEW --dport 53 -j ACCEPT
# iptables -A INPUT -p tcp -m state --state NEW --dport 53 -j ACCEPT
# service iptables save
# service iptables restart
-Konfigurasi awal:
# cp -R /usr/share/doc/bind-9.8.2/sample/var/named/* /var/named/chroot/var/named/
# cp -R /usr/share/doc/bind-9.8.2/sample/etc/* /var/named/chroot/etc/
# touch /var/named/chroot/var/named/data/cache_dump.db
# touch /var/named/chroot/var/named/data/named_stats.txt
# touch /var/named/chroot/var/named/data/named_mem_stats.txt
# touch /var/named/chroot/var/named/data/named.run
# mkdir /var/named/chroot/var/named/dynamic
# touch /var/named/chroot/var/named/dynamic/managed-keys.bind
# chmod -R 775 /var/named/chroot/var/named
# chmod -R 777 /var/named/chroot/var/named/data
# chmod -R 664 /var/named/chroot/var/named/slaves/
-Set if you don’t use IPv6 ( if use, don’t set it )
# echo 'OPTIONS="-4"' >> /etc/sysconfig/named
-Setting rndc.key
# rndc-confgen -a -c /etc/rndc.key
# chmod 755 /etc/rndc.key
-Konfigurasi /var/named/chroot/etc/named.conf
# vi /var/named/chroot/etc/named.conf
include "/etc/rndc.key";
options {
// Put files that named is allowed to write in the data/ directory:
directory "/var/named";
// "Working" directory
dump-file "data/cache_dump.db";
statistics-file "data/named_stats.txt";
memstatistics-file "data/named_mem_stats.txt";
pid-file "/var/run/named/named.pid";
/*Specify listenning interfaces. You can use list of addresses (';' is delimiter) or keywords "any"/"none" */
//listen-on port 53 { any; };
listen-on port 53 { localhost; 192.168.99.6; };
//listen-on-v6 port 53 { any; };
listen-on-v6 port 53 { ::1; };
//these are the ISP DNS or public DNS servers (optional)
forwarders {
203.130.208.18;
202.134.0.155;
203.130.193.74;
8.8.8.8;
8.8.4.4;
};
/* Access restrictions
There are two important options:
allow-query { argument; };
- allow queries for authoritative data
allow-query-cache { argument; };
- allow queries for non-authoritative data (mostly cached data)
You can use address, network address or keywords "any"/"localhost"/"none" as argument
Examples:
allow-query { localhost; 10.0.0.1; 192.168.1.0/8; };
allow-query-cache { ::1; fe80::5c63:a8ff:fe2f:4526; 10.0.0.1; };
*/
allow-query { localhost; 192.168.99.0/24; };
allow-query-cache { localhost; 192.168.99.0/24; };
// Enable/disable recursion - recursion yes/no;
recursion yes;
/* DNSSEC related options. See information about keys ("Trusted keys", bellow) */
/* Enable serving of DNSSEC related data - enable on both authoritative and recursive servers DNSSEC aware servers */
//dnssec-enable yes;
/* Enable DNSSEC validation on recursive servers */
//dnssec-validation yes;
/* Enable DLV by default, use built-in ISC DLV key. */
//dnssec-lookaside auto;
};
logging
{
/* If you want to enable debugging, eg. using the 'rndc trace' command,
* named will try to write the 'named.run' file in the $directory (/var/named).
* By default, SELinux policy does not allow named to modify the /var/named directory,
* so put the default debug log file in data/ :
*/
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
/* Views let a name server answer a DNS query differently depending on who is asking.
By default, if named.conf contains no "view" clauses, all zones are in the
"default" view, which matches all clients.
Views are processed sequentially. The first match is used so the last view should
match "any" - it's fallback and the most restricted view.
If named.conf contains any "view" clause, then all zones MUST be in a view.
*/
view "internal"
{
/* This view will contain zones you want to serve only to "internal" clients
that connect via your directly attached LAN interfaces - "localnets" .
*/
match-clients { localhost; 192.168.99.0/24; };
recursion yes;
zone "." IN {
type hint;
file "/var/named/named.ca";
};
/* these are zones that contain definitions for all the localhost
* names and addresses, as recommended in RFC1912 - these names should
* not leak to the other nameservers:
*/
include "/etc/named.rfc1912.zones";
// These are your "authoritative" internal zones, and would probably
// also be included in the "localhost_resolver" view above :
/*NOTE for dynamic DNS zones and secondary zones:
DO NOT USE SAME FILES IN MULTIPLE VIEWS!
If you are using views and DDNS/secondary zones it is strongly
recommended to read FAQ on ISC site (www.isc.org), section
"Configuration and Setup Questions", questions
"How do I share a dynamic zone between multiple views?" and
"How can I make a server a slave for both an internal and an external
view at the same time?"
*/
zone "bachem.local" IN {
type slave;
file "slaves/bachem.local.zone";
// allow-update { 192.168.99.5; };
// we assume we have a master dns server with the IP 192.168.99.5
masters { 192.168.99.5; };
allow-transfer { 192.168.99.5; };
};
zone "0.99.168.192.in-addr.arpa" IN {
type slave;
file "slaves/192.168.99.0.zone";
// allow-update { 192.168.99.5; };
// we assume we have a master dns server with the IP 192.168.99.5
masters { 192.168.99.5; };
allow-transfer { 192.168.99.5; };
};
};
-Restart Bind service & setting run level
# service named restart
# chkconfig named on
Make sure it’s running:
# rndc status
Note:
Jika tidak ada error, maka file zone dalam master server akan dicopy secara otomatis ke /var/named/chroot/var/named/slaves/
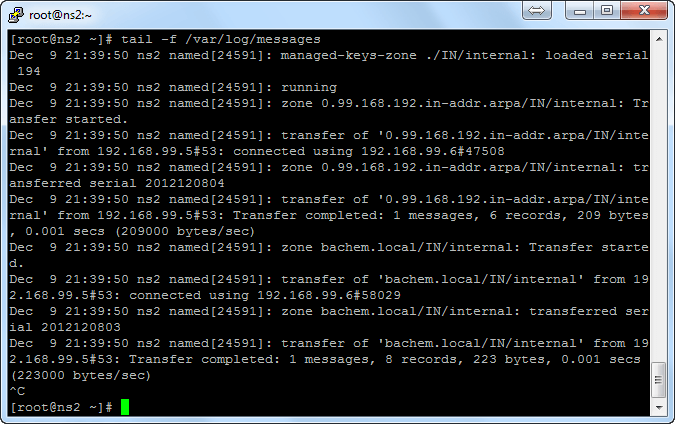
IV. Testing secondary DNS Query
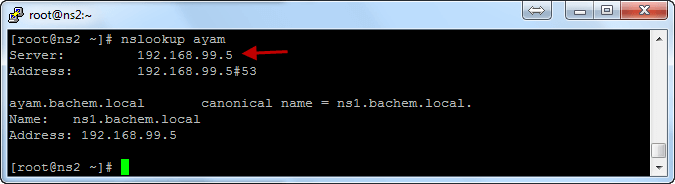
-Testing Primary DNS service start:
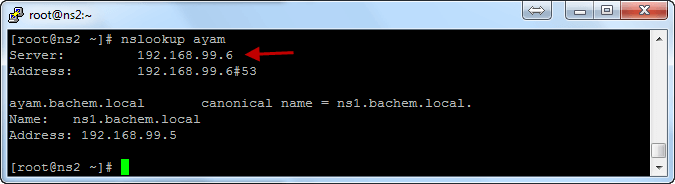
-Testing Primary DNS service stop :
References:
http://www.wains.be/index.php/2007/12/13/centos-5-chroot-dns-with-bind/
http://adlinux.blogspot.com/2010/04/chroot-dns-with-bind-centos-5.html
http://www.howtoforge.com/installation-of-bind-as-a-secondary-slave-dns-server-on-centos
http://doc.planet-lab.eu/html/x732.htm
http://docstore.mik.ua/orelly/networking_2ndEd/dns/ch10_15.htm
