-Install squidguard & squidguard-blacklist from rpmforge repo
# yum -y --enablerepo=rpmforge install squidguard squidguard-blacklists
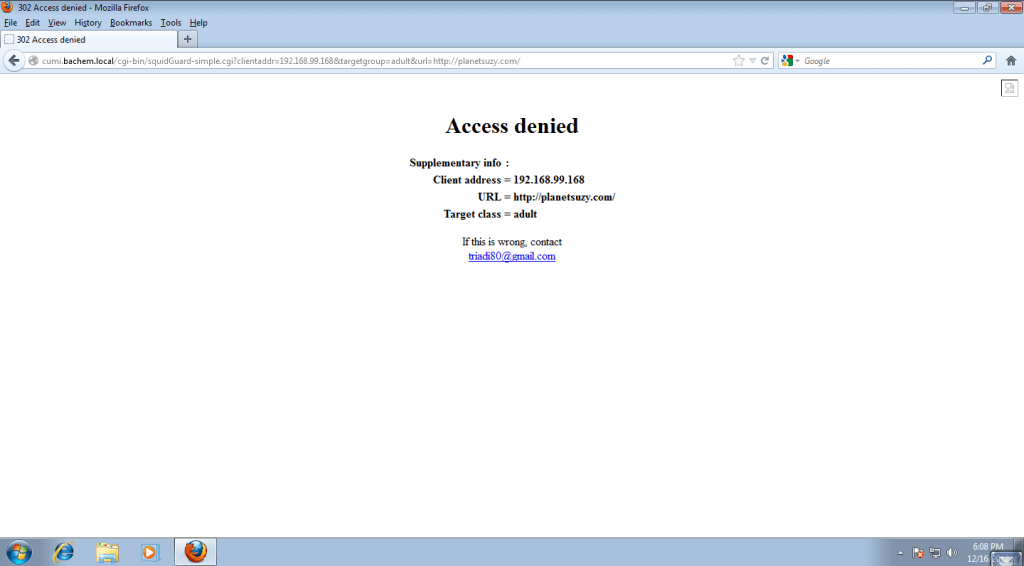
-Copy squidguard.cgi access denied page if you want to use it..
# cp /usr/share/doc/squidguard-1.3/squidGuard.cgi /var/www/cgi-bin/
# cp /usr/share/doc/squidguard-1.3/squidGuard-simple.cgi /var/www/cgi-bin/
-Backup file asli & edit squidguard.conf
# cp /etc/squid/squidguard.conf /etc/squid/squidguard.conf.bak
# vi /etc/squid/squidguard.conf
# CONFIG FILE FOR SQUIDGUARD
# See http://www.squidguard.org/config/ for more examples
# -------------------------------------------------------
dbhome /var/lib/squidguard
logdir /var/log/squidguard
# TIME RULES:
# abbrev for weekdays:
# s = sun, m = mon, t =tue, w = wed, h = thu, f = fri, a = sat
time workhours {
weekly mtwhfas 08:00 - 17:00
date *-*-01 08:00 - 17:00
}
# REWRITE RULES:
# -----------------
#rew dmz {
# s@://admin/@://admin.foo.bar.de/@i
# s@://foo.bar.de/@://www.foo.bar.de/@i
#}
# SOURCE ADDRESSES:
# -----------------
src admin {
ip 192.168.99.99
# user root foo bar
# within workhours
}
src managers {
ip 192.168.99.50-192.168.99.90
# user root foo bar
# within workhours
}
src users {
ip 192.168.10.100-192.168.10.254
# within workhours
}
### Generated blacklist definitions
### Group 'ads' containing entries for 'ads, publicite'
dest ads {
logfile ads.log
domainlist ads/domains
urllist ads/urls
# expressionlist ads/expressions
}
### Group 'adult' containing entries for 'adult, porn'
dest adult {
logfile adult.log
domainlist adult/domains
urllist adult/urls
# expressionlist adult/expressions
}
### Group 'aggressive' containing entries for 'aggressive, agressif'
dest aggressive {
logfile aggressive.log
domainlist aggressive/domains
urllist aggressive/urls
# expressionlist aggressive/expressions
}
### Group 'audio-video' containing entries for 'audio-video'
dest audio-video {
logfile audio-video.log
domainlist audio-video/domains
urllist audio-video/urls
# expressionlist audio-video/expressions
}
### Group 'drugs' containing entries for 'drugs, drogue'
dest drugs {
logfile drugs.log
domainlist drugs/domains
urllist drugs/urls
# expressionlist drugs/expressions
}
### Group 'forums' containing entries for 'forums'
dest forums {
logfile forums.log
domainlist forums/domains
urllist forums/urls
# expressionlist forums/expressions
}
### Group 'gambling' containing entries for 'gambling'
dest gambling {
logfile gambling.log
domainlist gambling/domains
urllist gambling/urls
# expressionlist gambling/expressions
}
### Group 'hacking' containing entries for 'hacking'
dest hacking {
logfile hacking.log
domainlist hacking/domains
urllist hacking/urls
# expressionlist hacking/expressions
}
### Group 'mail' containing entries for 'mail'
dest mail {
logfile mail.log
domainlist mail/domains
urllist mail/urls
# expressionlist mail/expressions
}
### Group 'proxy' containing entries for 'proxy, redirector, strict_redirector'
dest proxy {
logfile proxy.log
domainlist proxy/domains
urllist proxy/urls
# expressionlist proxy/expressions
}
### Group 'violence' containing entries for 'violence'
dest violence {
logfile violence.log
domainlist violence/domains
urllist violence/urls
# expressionlist violence/expressions
}
### Group 'warez' containing entries for 'warez'
dest warez {
logfile warez.log
domainlist warez/domains
urllist warez/urls
# expressionlist warez/expressions
}
### Define your local blacklists here
dest bad {
logfile localbad.log
domainlist local/bad/domains
urllist local/bad/urls
# expressionlist local/bad/expressions
}
dest good {
logfile localgood.log
domainlist local/good/domains
urllist local/good/urls
# expressionlist local/good/expressions
}
dest restrict {
logfile localrestrict.log
domainlist local/restrict/domains
urllist local/restrict/urls
# expressionlist local/restrict/expressions
}
acl {
admin {
pass any
}
managers {
pass good restrict !bad !adult !proxy any
}
users within workhours {
pass good !bad !restrict !ads !adult !audio-video !aggressive !drugs !gambling !hacking !proxy !violence !warez all
}
else {
pass good !bad !ads !adult !audio-video !aggressive !drugs !gambling !hacking !proxy !violence !warez all
}
default within workhours {
pass good !bad !restrict !ads !adult !audio-video !aggressive !drugs !gambling !hacking !mail !proxy !violence !warez all
#redirect 302:http://cumi.bachem.local/cgi-bin/squidGuard.cgi?clientaddr=%a&clientname=%n&clientident=%i&srcclass=%s&targetgroup=%t&url=%u
redirect 302:http://cumi.bachem.local/cgi-bin/squidGuard-simple.cgi?clientaddr=%a&targetgroup=%t&url=%u
}
}
-Create database good untuk lokal domain yg akan di whitelist permanen, bad untuk lokal domain yg akan di blacklist permanen dan restrict domain yang dibatasi selama jam kerja/workhours
# vi /var/lib/squidguard/local/good/domains
# white list domain
yahoo.com
yahoo.co.id
gmail.com
jobstreet.com
jobsdb.com
# vi /var/lib/squidguard/local/bad/domains
# block permanen
faithfreedom.org
faithfreedom.com
# mkdir /var/lib/squidguard/local/restrict/
# touch /var/lib/squidguard/local/restrict/domains
# touch /var/lib/squidguard/local/restrict/urls
# vi /var/lib/squidguard/restrict/domains
#domain yg dibatasi pada work hours
facebook.com
okezone.com
-Change permission /var/www/cgi-bin
# chmod -R 755 /var/www/cgi-bin/
-Ubah database blacklist menjadi format .db (berkeley DB) agar dapat diakses oleh squidguard
# squidguard -C all
-Ubah permission direktori /var/lib/squidguard/blacklist sesuai user squid
# chown -R squid:squid /var/lib/squidguard/blacklist
-Edit /etc/squid/squid.conf & add this script:
url_rewrite_program /usr/bin/squidguard -c /etc/squid/squidguard.conf
-Reload squid:
# squid -k reconfigure
-Example delete youtube.com domain from squidguard audio-video database
# vi /var/lib/squidguard/audio-video/domains
comment youtube.com
# squidguard -C /var/lib/squidguard/audio-video/domains
# squid -k reconfigure
-Example insert domain twitter.com to restrict database(list domain that block within workhours)
# vi /var/lib/squidguard/restrict/domains
twitter.com
# squidguard -C /var/lib/squidguard/restrict/domains
# squid -k reconfigure
References:
http://www.squidguard.org/